To maintain a competitive edge in the fiercely competitive business of manufacturing, companies must carefully walk the line between investing in new technologies and minimizing costs. In this pursuit of excellence, digital automation has emerged as a beacon of hope through its combination of software robotics, AI, and the Internet of Things (IoT), to reach unparalleled levels of productivity, quality, and scalability in the manufacturing industry.
This article explores the inherent benefits of employing business process automation software concerning manufacturing and its potential to revolutionize the industry. From enhancing production efficiency to addressing the skills gap, each aspect represents a stepping stone toward a more optimized, competitive, and future-proof manufacturing landscape.
Automation has begun to usher in a new era where traditional manufacturing methods and manual labor will soon be replaced with virtual software robots that work in conjunction with machines to perform workflows with greater accuracy, faster speeds, and absent human error.
How Can Digital Automation Help Companies in the Manufacturing Industry?
According to a recent study, if 64% of manufacturing tasks were automated 749 billion working hours would be saved globally. This statistic alone showcases how automation can increase workforce efficiency at any business, provided solutions are implemented properly:
1. The Efficiency Leap: Enhancing Production Efficiency through Automation
One of the most evident benefits of automation lies in its ability to elevate production efficiency to unprecedented heights. Manufacturing operations that leverage automation technologies witness a significant reduction in cycle times and an increase in output. Machines, unaffected by fatigue, work continuously, leading to a continuous and consistent flow of production. As a result, businesses can meet growing demands while reducing lead times, ensuring on-time deliveries, and bolstering customer satisfaction.
2. The Pursuit of Perfection: Ensuring Product Quality and Consistency
In a highly competitive market landscape, product quality is paramount in determining a manufacturer’s success. Human errors are unavoidable, and even the most skilled workers can falter under monotonous and repetitive tasks. Automation, with its precision and reliability, eradicates variations, leading to uniformity and superior product quality. By implementing automated manufacturing systems in quality control processes, manufacturers can achieve a remarkable reduction in defects and rejections, saving both time and resources.
3. Prioritizing Safety: Improving Workplace Safety Through Automation
Employee safety is a cornerstone of responsible manufacturing practices and is dramatically enhanced when automation solutions are implemented. The integration of automation technology mitigates risks by reducing the involvement of human workers in hazardous or physically demanding tasks. Business process automation tools excel in handling dangerous materials and environments, leading to a dramatic decrease in workplace accidents and ensuring a safer work environment for all. Moreover, this fosters a positive work culture, improving employee morale and retention rates.
4. Smart Resource Management: Optimizing Resources with Automation
Resource management plays a pivotal role in operational efficiency and sustainability. Automation aids manufacturers in optimizing the use of resources such as raw materials, energy, and time. By streamlining processes, automating energy-intensive tasks, and minimizing waste, businesses can reduce their environmental footprint and embrace a greener approach to manufacturing. This not only aligns with the rising demand for eco-friendly products but also establishes the brand as a responsible corporate citizen.
5. Embracing Agility: Flexibility and Scalability in Manufacturing
The business landscape is perpetually evolving, and manufacturers must adapt swiftly to changing market demands. Automation empowers companies to embrace agility by offering unparalleled flexibility and scalability. Automated systems can be quickly reprogrammed and reconfigured to accommodate different product specifications, sizes, and configurations. Consequently, businesses will be more equipped to seize new market opportunities, pivot their production lines, and respond promptly to customer demands, gaining a competitive edge in the dynamic marketplace.
6. Empowering Data-Driven Decision Making
As Industry 4.0 continues to transform the manufacturing landscape, data has emerged as a valuable asset. Automation integrates sensors and IoT devices that gather real-time data on production performance, machine health, and quality metrics. This treasure trove of information empowers manufacturers to make data-driven decisions, optimize processes, predict maintenance requirements, and identify potential bottlenecks. The ability to leverage data effectively equips businesses with a strategic advantage, propelling them toward continuous improvement and operational excellence.
7. Bridging the Skills Gap: Collaborative Automation
The manufacturing sector has been grappling with a skills void, where the demand for skilled workers exceeds the available workforce. Automation offers a solution to this challenge through collaborative robotics or cobots. These robots work alongside human operators, handling repetitive or physically demanding tasks, while human workers focus on more complex and creative aspects of production. Collaborative automation not only bridges the skills gap but also augments human potential, fostering a harmonious and productive human-machine partnership.
How to Automate Manufacturing?
Automating manufacturing processes is a key step toward streamlining operations and maximizing productivity. Here’s a concise guide to help you navigate the journey of automation:
Assess Your Processes: Begin by evaluating your existing manufacturing workflows. Identify manual, high-volume, and repetitive tasks as areas with automation potential.
Set Clear Objectives: Define your automation goals, whether it’s to increase output, reduce errors, or enhance quality. Clear objectives will guide your automation strategy.
Choose the Right Technology: Select automation solutions that align with your specific needs. Explore options like robotics, AI-powered systems, or IoT devices, depending on your industry and requirements.
Start with a Pilot Project: Launch a small-scale pilot to test the effectiveness of automation in a controlled environment. Analyze the results and gather feedback to refine your approach.
Integrate Seamlessly: Ensure that your business process automation solution integrates smoothly with existing systems. This fosters a cohesive and efficient manufacturing ecosystem.
Train Your Workforce: Empower your employees with the skills needed to work alongside automated systems. Encourage a collaborative mindset that values automation as a tool for productivity enhancement.
Monitor and Optimize: Continuously monitor the impact of automation on key performance indicators. Use data insights to optimize processes and make data-driven decisions.
Scale Gradually: Expand automation gradually across different processes and departments as your team becomes more comfortable with the technology.
Prioritize Data Security: Implement robust cybersecurity measures to safeguard sensitive data, ensuring compliance with regulations and protecting your company’s reputation.
Embrace the Future: Embrace the principles of Industry 4.0 to unlock the full potential of automation and prepare your manufacturing business for a dynamic and competitive future.
Benefits of Automation in Manufacturing
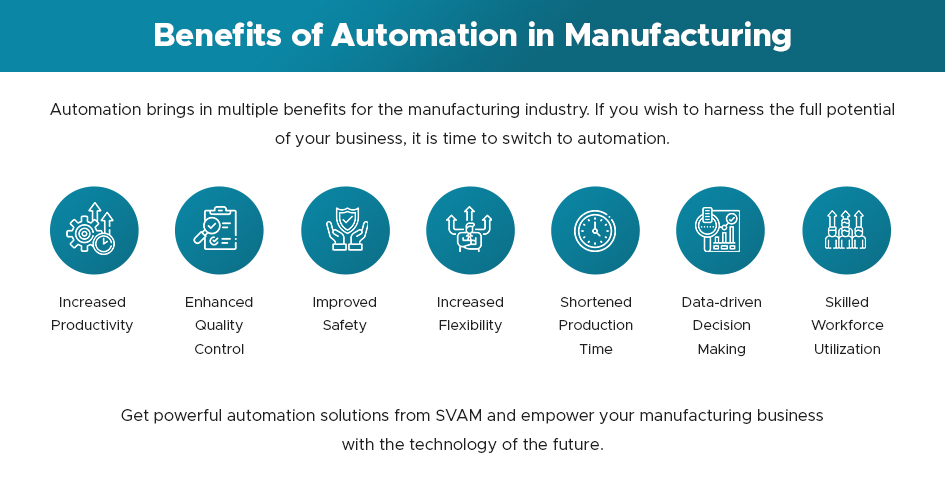
Automation brings multiple benefits to the manufacturing industry. If you wish to harness the full potential of your business, it is time to switch to automation.
- Increased Productivity
- Enhanced Quality Control
- Improved Safety
- Increased Flexibility
- Shortened Production Time
- Data-driven Decision Making
- Skilled Workforce Utilization
Get powerful automation solutions from SVAM and empower your manufacturing business with the technology of the future.
Experience the Benefits of Automation in Manufacturing
Automation has ushered in a new era of manufacturing, where efficiency, quality, safety, and flexibility converge to drive optimal growth and profitability. From enhanced production efficiency to data-driven decision-making business process automation services can help with each aspect of automation.
SVAM International, Inc. is a global leader in combining RPA with AI and Machine Learning (ML) and excels in automating repetitive tasks intelligently for its clients. By bridging the gap between intelligent automation and artificial intelligence, we effectively minimize staffing expenses and mitigate the potential for human errors. Our expertise lies in creating seamless solutions that optimize efficiency and drive productivity for our valued clients.
A growing number of organizations (36%) are using business process management software to automate workflows, with 50% of business leaders planning to automate more repetitive tasks. If you wish to join the bandwagon of growth, it’s time to connect with SVAM.