In February 2023, T-Mobile, a wireless telecommunication provider, announced that a bad actor had gained access to some customer data through a vulnerable API. As per their declaration, sensitive data like payment card information, or social security numbers were stolen in the breach. Incidents like these aren’t new as cyber crimes are increasing by leaps and bounds with each passing year.
The prediction is that $8 trillion will be lost to cyber crimes by the end of 2023, which is almost a third of the USA’s GDP in 2022 and twice as much as India’s projected GDP in March 2023. The global loss to cybercrime will grow more than 15% year by year to reach $10.5 trillion by 2025.
Even though there are various traditional cyber security models embedded in the business’ infrastructure, many IT experts witnessed a leak in their cloud security models. The compromised security and increased concerns of attacks, especially after remote working, have led them to resort to the ZTNA (Zero Trust Network Access).
Organizations have increasingly used Zero Trust security over the past few months to manage the cyber war and to pull the levers of their compromised channels.
Thus, more digitization and more compromised security means a need for more robust security measures for which ZTNA is the ideal choice.
What is Zero Trust?
Zero Trust is a security framework that implies that before granting or maintaining access to applications and data, all users—whether inside or outside the organization’s network—must first authenticate, authorize, and undergo ongoing security configuration and posture validation. Zero Trust is based on the principle that you should not trust internal or external resources and that there is no such thing as a traditional network edge.
The current digital transformation uses the Zero Trust framework to secure data and infrastructure. It covers issues such as ransomware threats, cloud infrastructures, and hybrid or remote working models.
Being a complex entity until the companies start using the ZTNA at large, many organizations have come up with their own definitions of Zero Trust.
SVAM International, in their constant efforts to boost the cyber security measures and provide highly robust solutions, can help you identify, implement, and understand the right cybersecurity program including zero trust. They have also partnered with Tanium, to further enhance their suite of end-to-end security solutions.
Principles of Zero Trust
Zero trust software works on three principles. It’s because of these principles that zero trust stands out of the crowd of other cyber security solutions.
1. Never trust, always verify: This principle states that every device, application, person, website, and data should be addressed as a threat or untrusted for a zero-trust system.
2. Verify Rigorously: No device or data should have the advantage of non-verified authentication and should be highly verified before granting access.
3. Assume Breach: Manage and protect resources as if the threat is already present in the area. Every use should be checked by fault, examine each user, data flow, and authorization request. It also states that all network traffic should be constantly monitored for breaches or any breach-like activity.
What is the Need for Zero Trust?
As discussed earlier in the article, there is a dire need for end-to-end security measures and risk analysis. Owing to the need, 75% of firms have realized that they need to update the already existing technological infrastructure as it is necessary to manage emerging cyber risks and ensure that Zero Trust software principles are incorporated into cloud adoption models from the beginning.
In order to strengthen cyber security, organizations can make ongoing security procedures more robust so that businesses can devote more time to innovative tasks rather than worrying about security.
It may be surprising that even though the concept of ZTNA is on the rise, 44% of companies need assistance in choosing and implementing the best zero-trust model. Additionally, nearly two-thirds of businesses feel that their teams lack the time, knowledge, and skills necessary to successfully roll out best practices for zero trust throughout the company.
What’s more intriguing is that the businesses that are already familiar with the model cannot fully comprehend how to put ideas into practice since they are unsure of how and where to implement a Zero Trust strategy in order to bolster their individual security plans.
This is where a cybersecurity company led by the subject matter experts comes in!
SVAM International, as a leading cybersecurity organization, knows what it takes to establish and integrate the solutions that can help enhance security measures. Our experts can help find the right zero trust model and assist in implementing the same the right way across the organization.
Before we jump to the solution, let’s see the trends that will make zero trust security a Top Business Priority in 2023.
Reasons Why Zero Trust Will Be a Business Priority in 2023
We need more measures to secure the data and businesses in the online world where hackers are trying to breach accounts, leak data, and gain monetary benefits from ransomware attacks. This is why zero trust is the need of the hour.
Here are a few reasons why zero trust will be a top business priority 2023.
1. Compliance will be a top business priority
Having data compliance is challenging for companies owing to the rigidity of each data privacy law. Adding to the challenge is the fact that the companies that have not taken the necessary precautions to protect data are subject to substantial fines under the data privacy regulations. Thus, it becomes highly imperative to protect the data and comply with the data regulation.
All the futuristic businesses concerned about data protection would want to have a data-centric focus to significantly reduce the danger of an eventual breach. Through the strategy, businesses can protect data even if a breach occurs.
SVAM International can help you build the right infrastructure for end-to-end data protection and risk analysis even before the breach happens, reducing the chances of exponential loss and increasing the chances of data recovery.
2. Data security will be an organizational concern
Cyber security is not just the concern of the CXO level, it has now creeped down to the employee level. It is believed that most data breaches occur at the lower levels as not every employee has knowledge about data security.
The businesses will prioritize data security and protection as a result of this convergence of usage. Owing to the same, 62% of respondents anticipate an increase in their security budget of up to 10% in 2023.
Whatever the current use of the data is, companies will look into ways to protect it. Data security issues will be the main driver of privacy compliance in 2023. Companies will increase their efforts in data protection as penalties for breaking privacy laws become more common.
3. Zero trust will accelerate data protection
In contrast to the regular security measures that offer minimal security, the organizations will go above and beyond the most fundamental security precautions for data protection strategies. The paradigm shift to zero trust model is a testament to how priceless that data is, and the non-compromisable need to always protect it, whether it is being used or stored.
Organizations looking to reduce data risk must assume a breach has occurred in order to eliminate the risk. Businesses that are aware of this will use proactive protection techniques at the record level, making data inaccessible to hackers. As they contribute to enhancing corporate reputation and fostering customer trust, these actions are advantageous for business.
3. A possible recession will drastically increase data’s value
In the last few months, companies like Meta, Twitter, Goldman Sachs, Amazon, and DoorDash have been laying off employees at a startling rate. According to Inc.42, as of December 8, 2022, 17,989 employees were laid off by 52 Indian startups, including several unicorns. Unfortunately, many warning signs are pointing to an impending recession. In such a scenario, companies will rely on data more than ever to get valuable insights that can help make data-driven decisions, discover emerging market trends, and strategize sales.
Given the critical nature of data insight during potential recessions, organizations must employ methods that allow continuous analysis while protecting data at all costs.
4. Transition from data stores to data pipelines
Decision makers at the CXO level are aware of how important data is for every decision. The steadily rising investments in data processing infrastructure and data engineering staff serve as the best possible example. Companies, more than ever, now rely on the data pipeline, which serves as the channel for data insight.
The breach of data pipelines, whether deliberate or unintentional, can result in non-compliance, lost revenue, and reputational harm. Businesses will invest more heavily in privacy measures to process data without disclosing it.
Zero Trust Use Cases
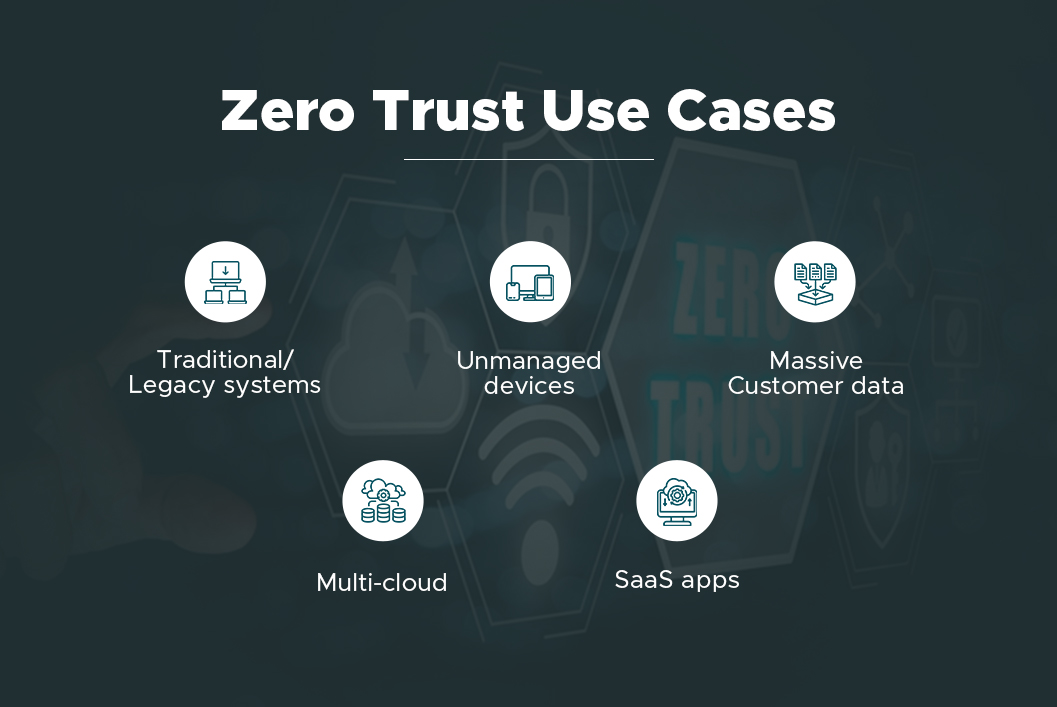
Zero trust has always been a highly robust solution to avert cyber attacks. While all the companies can employ Zero trust software and benefit from it, you must integrate it into your business immediately if your infrastructure deployment model includes:
- Traditional/Legacy systems
- Multi-cloud
- Unmanaged devices
- Massive Customer data
- SaaS apps
With Zero Trust Security, You Can Address Key Threats
Cyber attacks– These can occur when there are unmanaged devices, remote working, data exchange through various resources, phishing mails
Ransomware – threats and attacks causing compromised identity, code execution, and massive data loss
Insider threats – Analysis of behavioral analytics for remote users is particularly difficult.
Get the SVAM Support & Protect Yourself Today
For a successful Zero Trust model to be realized, micro-segmentation technologies and Zero Trust Network Access (ZTNA) are essential technical foundations.
Why? Because businesses should effectively react to the changing cyber realities of today. Organizations must now prepare for the inevitable and analyze the risk rather than just planning for the possibility of a cybersecurity catastrophe.
We, at SVAM International, have more than 30 years of combined experience defending companies against such attacks and averting any loss of data, operational capability, or infrastructure.
We have recently partnered with Tanium, a leading cybersecurity provider, to make our solutions better and provide an enhanced experience for the companies.
By developing strong security solutions based on cutting-edge digital technologies, SVAM International has been able to stop multiple security breaches. Get in touch with us today to learn more about the Zero Trust software.