Cybersecurity is a growing concern across all industries, but certain sectors, such as public services, educational institutions, healthcare, and mid-sized businesses, are particularly vulnerable. The increasing sophistication of cyber threats, coupled with greater reliance on digital infrastructure, makes it essential to proactively address security vulnerabilities. This white paper explores the primary cybersecurity challenges in these sectors, with a focus on the healthcare industry, the impact of breaches, and recommended strategies for enhancing cybersecurity defenses.
The healthcare industry is undergoing significant growth due to a variety of factors, including advancements in medical technology, demographic changes, and evolving patient expectations. This expansion is driven by the aging population, the rising prevalence of chronic diseases, and innovations in healthcare delivery such as electronic health records (EHRs), telemedicine, and connected medical devices.
Additionally, both governments and private sectors are investing heavily in healthcare infrastructure, including hospitals, clinics, and long-term care facilities. Mergers, acquisitions, and partnerships are further expanding the reach of healthcare networks, improving service delivery, and reducing costs.
However, with this digital transformation comes heightened cybersecurity risks. The healthcare industry is a prime target for cybercriminals due to the high value of sensitive medical data and the critical nature of its services. Cyberattacks in healthcare can have severe consequences, affecting both patient safety and operational integrity.
The healthcare sector is particularly vulnerable to cyberattacks due to the sensitive nature of the data it handles, the complexity of its digital systems, and its reliance on technology.
Some of the key cybersecurity risks in healthcare include:
- Sensitive Personal Information
Healthcare data contains highly sensitive personal details, including names, addresses, social security numbers, insurance details, and medical histories. This information is highly valuable to cybercriminals as it can be used for fraud, identity theft, medical fraud, and blackmail. - Medical Identity Theft
Stolen healthcare data can be used for medical identity theft, where criminals use a patient’s identity to receive medical care, obtain
prescription drugs, or file false insurance claims. Unlike financial information, medical records are difficult to recover or change,
making this data particularly attractive to attackers. - Interconnected Devices and Systems
Healthcare facilities use a variety of interconnected systems, such as EHRs, medical devices, and hospital networks. The complexity of these systems creates multiple entry points for attackers, where a breach in one system can quickly - Legacy Systems
Many healthcare organizations still rely on outdated systems that are difficult to secure and update, making them prime targets for cyberattacks. Legacy systems often lack modern security features, leaving gaps for attackers to exploit - Ransomware Attacks
Healthcare providers are frequent targets for ransomware attacks, where attackers encrypt critical
data and demand payment to restore access. Due to the critical nature of healthcare services, organizations are more likely to comply with ransom demands to avoid disruptions in patient care. - Internet of Medical Things (IoMT)
The growing number of connected medical devices, including pacemakers and insulin pumps, increases the risk of cyberattacks. Many of these devices were not designed with security in mind, making them vulnerable to exploitation. - Insider Threats
Healthcare organizations are also vulnerable to insider threats, where employees or contractors misuse their access to sensitive data or introduce malware into the system, either intentionally or unintentionally. - Lack of Cybersecurity Awareness
Many healthcare staff lack adequate cybersecurity training, making them more susceptible to phishing scams, social engineering attacks, and weak password management.
Human error remains a leading cause of cyber incidents in the healthcare sector. - Resource Allocation
In healthcare, a significant portion of the budget is allocated to patient care, often leaving cybersecurity as a lower priority. With limited resources, organizations may struggle to address evolving cyber threats effectively - Limited Budgets
Many healthcare organizations, particularly smaller facilities, operate with limited cybersecurity budgets.
As a result, they may not invest sufficiently in advanced security tools, leaving them more vulnerable to cyber threats. - Telemedicine and Remote Care
The rapid adoption of telemedicine during the COVID-19 pandemic has introduced new cybersecurity risks.
Many telemedicine platforms may not have been designed with strong security measures, making them potential targets for cyberattacks. - Disruption to Patient Care
Cyberattacks that disable hospital systems, delay surgeries, or prevent access to medical records can have life-threatening consequences.
Attackers exploit this urgency, knowing that healthcare organizations are likely to pay ransoms to restore services quickly. - Cloud-Based Systems
The increased use of cloud services to store healthcare data and manage operations creates additional security risks. Misconfigurations, weak encryption, and inadequate access controls can lead to data leaks or unauthorized access. - Third-Party Risks
Healthcare organizations frequently work with third-party vendors, including medical device manufacturers and software providers. These vendors may have access to sensitive data but may not meet the same security standards, making them weak links in the security chain. - Nation-State Attacks
Nation-state actors often target healthcare organizations for espionage or political motives.
State-sponsored attackers may seek to steal sensitive research data, such as vaccine development information or clinical trial results, making these organizations particularly attractive to sophisticated and well-funded attackers.
What Needs to be Done
Although the healthcare industry is governed by strict regulations regarding the protection of personally identifiable information (PII) and protected health information (PHI)—such as HIPAA in the U.S.—many larger hospital facilities, despite heavy investments in cybersecurity, continue to experience frequent cyberattacks for various reasons previously mentioned.
Smaller medical facilities, however, face even greater cybersecurity risks due to their limited financial resources, reliance on outdated systems, lack of dedicated cybersecurity personnel, and overall weaker defenses. Their dependence on legacy systems, insufficient employee training, and inadequate data protection strategies leave them vulnerable to a broad range of cyber threats, including ransomware attacks and data breaches. In many cases, they may also fail to fully comply with HIPAA or other regulatory requirements.
For larger healthcare organizations, reducing risk is even more complex, as they often manage their own IT environments. This necessitates an independent, comprehensive review of their entire information technology infrastructure, including physical security measures.
A cybersecurity assessment should thoroughly evaluate the organization’s security posture, encompassing everything from technical defenses to governance and regulatory compliance. By identifying vulnerabilities, monitoring threats, and preparing for potential incidents, an organization can build a more resilient defense against cyberattacks and improve its overall security strategy. Such assessments should culminate in actionable recommendations to address gaps, strengthen defenses, and mitigate risks.
The review should include the following key areas:
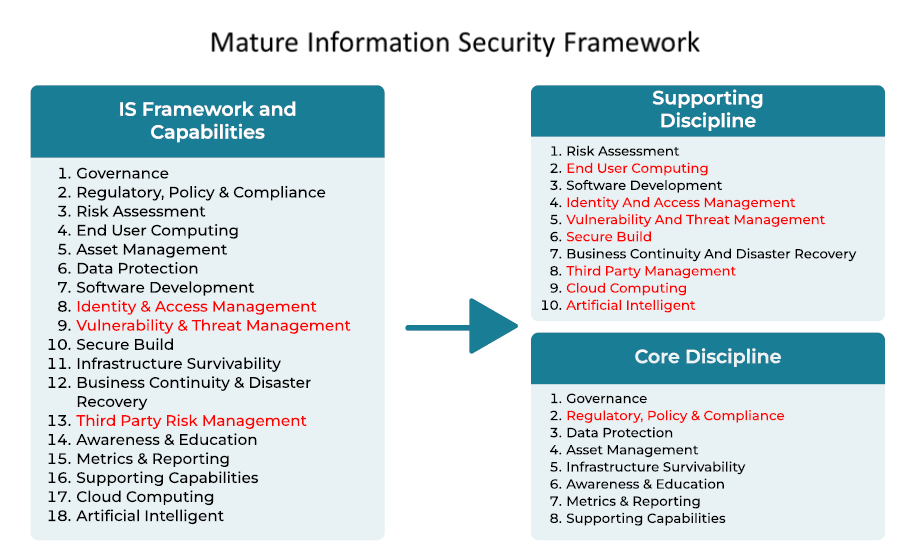
There are several cybersecurity assessment frameworks, such as the NIST Cybersecurity Framework (NIST CSF), that are widely recognized and adopted across various industries to help organizations evaluate their security posture, identify vulnerabilities, and implement effective cybersecurity controls. The best framework for an organization depends on its industry, regulatory requirements, size and specific security needs.
Developed by the U.S National Institute of Standards and Technology (NIST), the NIST Cybersecurity Framework s one of the most respected and widely used frameworks. It provides organizations with guidelines to manage and reduce cybersecurity risk effectively.
Regardless of which framework is selected, the assessment must be conducted by an experienced and knowledgeable firm. This ensures that all assets, including third-party dependencies, are accounted for. Moreover, findings should be risk-rated and accompanied by a remediation plan aligned with the organization’s risk appetite.
Large healthcare providers can significantly benefit from adopting a Zero Trust security model, which greatly enhances their defense mechanisms. Zero Trust continuously verifies users and devices, segments networks, and sensitive patient data, secure loTs devices and comply with regulatory standards like HIPAA.
As cyber threats become more sophisticated, the Zero Trust model offers a proactive, resilient, and adaptable approach to safeguarding healthcare organizations against breaches, ransomware, and other cyber risks Achieving Zero Trust is not trivial, but it is becoming increasingly necessary for large enterprises, especially hospitals and healthcare facilities. With the rise of generative AI, the sophistication and frequency of cyberattacks have increased tenfold, posing a major challenge for CIOs and CISOs in securing their environments.
Zero Trust operates on the principle that no user, device, or transaction should be trusted by default, regardless of their location, credentials, or network connection. Key components of Zero Trust include network segmentation, micro-segmentation, identity and access management (IAM), continuous authentication and authorization, least privilege access, network and data encryption, threat intelligence, and continuous monitoring.
Achieving Zero Trust is a journey that begins with a thorough understanding of an organization’s assets (hardware, software, people, and locations), the criticality of these assets, and how they are interconnected and accessed. Applying the principle of least privileged access can only be effective when you have full visibility of your assets and who or what can access them. This raises the question: how many organizations truly have a comprehensive picture of their assets and the maturity of their Identity and Access Management (IAM) systems? This is especially relevant to the healthcare industry, which is continuously evolving and facing a vast and expanding attack surface.
Key Challenges in Implementing Zero Trust:
- Zero Trust Complexity: Implementing Zero Trust is complex, requiring a deep understanding of an organization’s network, applications, and data flows. Designing a comprehensive architecture, including microsegmentation and access controls, is especially challenging in large environments.
- Legacy Systems: Integrating legacy systems into a Zero Trust framework is challenging due to their lack of modern security features or the need for significant modifications.
- User Experience: Zero Trust controls, like multi-factor authentication, may impact user experience and productivity. Ensuring security with a seamless user interface is crucial.
- Cultural Shift: Zero Trust requires a cultural shift, moving from a perimeter-based security mindset to continuous verification. Investing in user education is essential to overcome resistance.
- Operational Challenges: Managing access controls, segmentation policies, and authentication mechanisms presents operational challenges in complex environments.
- Integration: Zero Trust often requires integration with existing security technologies. Ensuring compatibility and smooth integration is challenging and requires careful planning.
- Scalability: As organizations grow, maintaining a scalable Zero Trust architecture becomes challenging. Handling increasing traffic, user volumes, and data volumes without compromising performance is crucial.
- Compliance: Zero Trust implementations must align with industry regulations. Ensuring solutions meet compliance standards and generate necessary audit logs is essential.
As mentioned earlier, the journey towards achieving Zero Trust should begin with a comprehensive assessment conducted by an experienced entity with deep expertise in cybersecurity controls. This entity should work closely with key stakeholders, including business owners, to accurately identify gaps and potential risks. A well-defined strategy with a clear roadmap is essential for taking the appropriate steps toward achieving Zero Trust, or at least approaching near-Zero Trust status.
Additionally, organizations must establish Key Risk Indicators (KRI), Key Operational Indicators (KOI), and Key Performance Indicators (KPI) to effectively measure the safety, soundness, and overall cybersecurity posture of the company.
For the healthcare industry, having a fully developed and thoroughly tested Disaster Recovery and Incident Management plan is critical, as any downtime can have serious, even life-threatening, consequences.
Smaller healthcare entities—including doctor’s offices, urgent care facilities, nursing homes, and assisted living centers—may have a smaller attack surface, but they often lack the necessary in-house IT expertise, have limited budgets, and may rely on third-party IT providers to manage their environments. In many cases, these organizations may not fully understand their risks, and their internal or third-party managed IT providers (MSPs) may not offer adequate cybersecurity protections.
These smaller healthcare organizations would also benefit from a complete security assessment to identify vulnerabilities and partner with a service provider that offers not only mature managed IT services but also a strong cybersecurity team to properly safeguard their operations.
Conclusion
The healthcare industry faces unique cybersecurity challenges due to its reliance on sensitive data, interconnected systems, and digital infrastructure. While technology is revolutionizing healthcare, it also introduces significant vulnerabilities that must be addressed. To mitigate these risks, healthcare organizations must understand their overall risk, invest in robust cybersecurity measures, enhance staff training, and develop comprehensive incident response plans. Without these proactive steps, the healthcare sector will remain a prime target for cyberattacks, with potentially devastating consequences for both patients and providers.
About the Author
Kambiz Mofrad is a highly accomplished senior executive and subject matter expert in Cybersecurity, Artificial Intelligence, Technology, and Data Privacy, with extensive leadership and implementation experience. His career has focused on resolving complex enterprises and regulatory challenges. In his current role, Kambiz serves as the Chief Information Security Officer (CISO) at SVAM International, with additional responsibilities as the Head of Global Infrastructure and acting Chief Cyber Security Architect.
With nearly three decades of experience at Citigroup in various risk management and technology leadership positions, Kambiz has a remarkable track record of exceeding corporate objectives.

Kambiz Mofrad
CISO / Managing Director
SVAM International
Throughout his career, he has demonstrated comprehensive expertise in technical development, information security, supplier risk management, operational management, data governance, and delivering best-in-class technology solutions for global and institutional clients.



